8.3 million plaintext passwords exposed in DailyQuiz data breach
The personal details of 13 million DailyQuiz users have been leaked online earlier this year after a hacker breached the quiz builder's database and stole its content, which he later put up for sale.
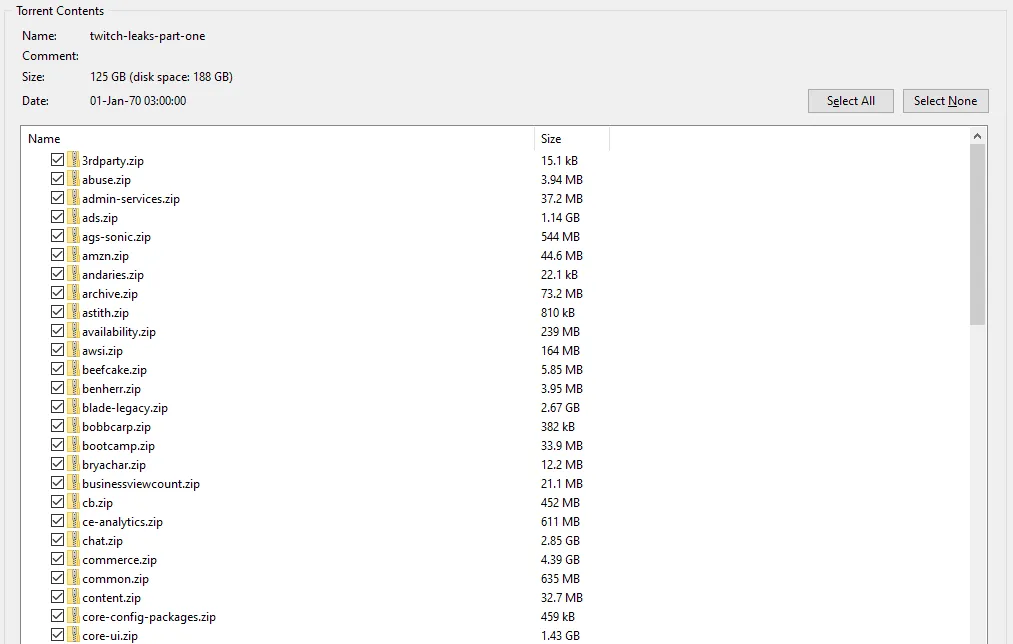
The data, of which The Record has obtained copies from two different sources, contains details about 12.8 million users, including plaintext passwords, emails, and IP addresses for 8.3 million accounts.
The stolen data has been sold on hacking forums and Telegram channels since January 2021 for a price of $2,000 paid in cryptocurrency, but leaked into the public domain this month, after it was exchanged through different data brokers, and eventually came into the hands of a security researcher, who shared it with The Record.
The data has also been provided to Have I Been Pwned, a website operated by Australian security researcher Troy Hunt. DailQuiz users can visit the Have I Been Pwned website and see if their personal details were exposed in the site's security breach.
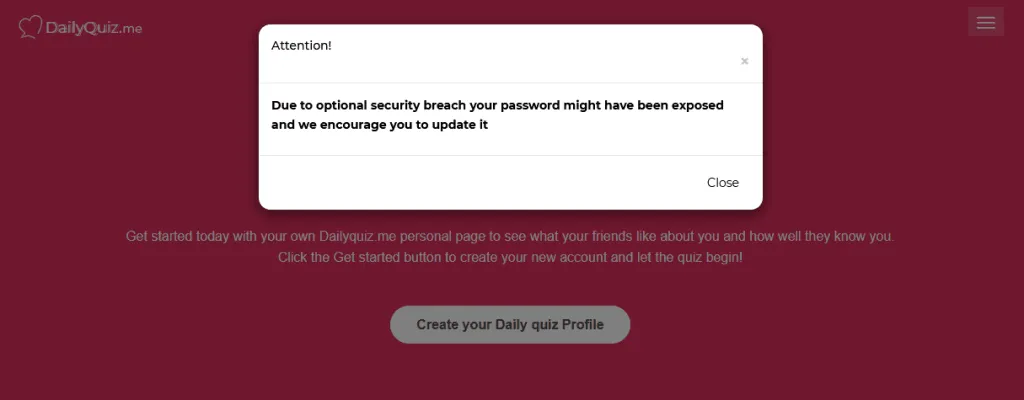
DailyQuiz (formerly known as ThisCrush), which allows users to register accounts and build sharable quizzes, has admitted to the security breach through a popup that is currently displayed on its website.
A request for comment seeking additional details about its security incident was not returned before publication.
The company may have some explaining to do, especially when it comes to storing users' passwords in plaintext, a big security no-no.
However, DailyQuiz is not the first nor will it be the last company that makes the mistake of storing passwords in plaintext. Others that made the same mistake also include the likes of Russian social media giant VK, Italian email provider Email.it, stock trading service Robinhood, Google's G Suite platform, and even social media giant Instagram.
Current risks to DailyQuiz users
While there is a danger that miscreants or abusive partners might access DailyQuiz accounts seeking information on their owners, there is also the risk to users' other online accounts.
Cybercriminal groups collect breaches like the DailyQuiz one and use the data to carry out credential stuffing attacks — where they check a person's DailyQuiz username/email and password combination at other online services in an attempt to hijack other accounts.
Credential stuffing attacks are fueled by leaks like these, as it allows the attackers to use the plaintext passwords right away, without having to expend huge computational and financial resources to crack hashed passwords (the format in which most passwords are stored).
DailyQuiz users who know they reused their username, email, and password on other sites are advised to change them right away. Accounts tied to social media profiles or that hold any type of financial information should be checked and updated first.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.