Three Russians, one Kazakhstani charged in takedown of Anyproxy and 5socks botnets
Two powerful botnets have been dismantled by law enforcement agencies and the alleged administrators now face criminal charges, U.S. prosecutors said Friday.
The Justice Department said it seized the domain names Anyproxy.net and 5socks.net — with both sites now featuring a law enforcement takedown banner. The banners say the websites were disrupted in an operation called “Moonlander.”
Three Russian nationals — 37-year-old Alexey Viktorovich Chertkov, 41-year-old Kirill Vladimirovich Morozov and 36-year-old Aleksandr Aleksandrovich Shishkin — were charged with conspiracy and damage to protected computers for their role in running botnet services offered through Anyproxy and 5socks. Kazakhstani national Dmitriy Rubtsov, 38, was hit with the same charges.
The Justice Department did not say where the men are currently based.
The four created the botnets by infecting older-model wireless internet routers in the U.S. and abroad. A malware campaign allowed the men to reconfigure the routers and offer them for sale as proxy servers through the Anyproxy and 5socks sites.
The 5socks.net website offered more than 7,000 proxies for sale and allowed users to pay monthly fees of up to $110 for access.
The Justice Department said the website domains were managed by a company based in Virginia and that the four men allegedly earned about $46 million through the infected routers over a 20-year stretch.
The notice coincides with an alert released by the FBI on Wednesday warning people that end-of-life routers that are no longer supported by the companies that made them were the primary target of the administrators behind Anyproxy and 5socks.
The advisory notes that Chinese cyber actors “are also among those who have taken advantage of known vulnerabilities in end of life routers and other edge devices to establish botnets used to conceal hacking into US critical infrastructures."
The routers listed in the advisory include older models from Linksys or Cisco.
Chertkov and Rubtsov were slapped with additional charges of false registration of a domain name after they used fake identities to register the domains.
The investigation was run out of the Oklahoma City FBI office after multiple businesses and homes in the state were found to have routers infected with the malware used in the campaign.
U.S. officials worked with law enforcement in Thailand and the Netherlands on the operation as well as Lumen Technologies’ Black Lotus Labs. The company posted a technical analysis of the operation on its blog, reporting that it tracked a “weekly average of 1,000 unique bots in contact with the command-and-control (C2) infrastructure, located in Turkey.”
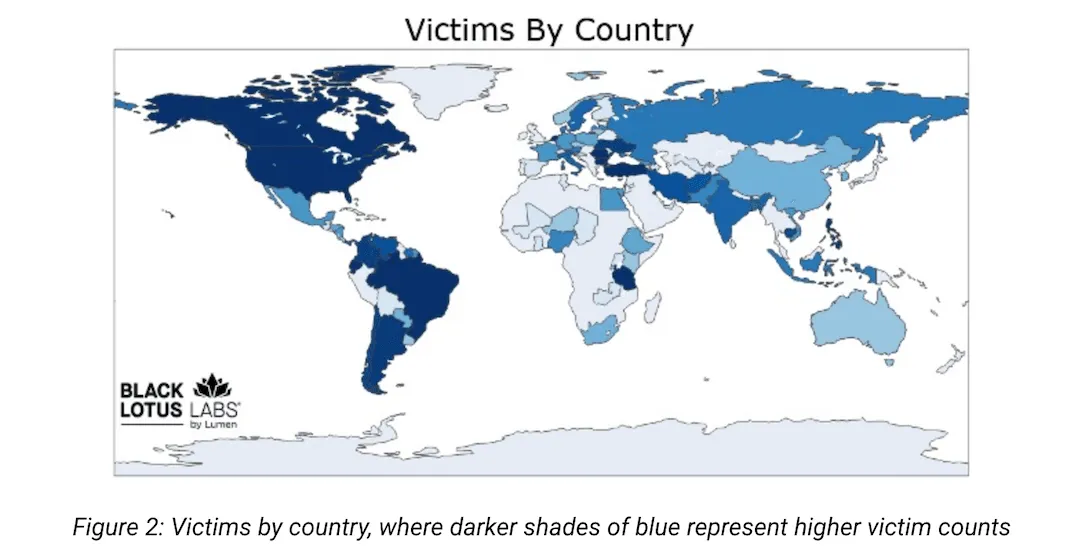
Black Lotus Labs' map showing the concentration of botnet victims.
“Over half of these victims are in the United States, with Canada and Ecuador showing the next two highest totals,” the researchers said. “Based on Black Lotus Labs’ telemetry, we can see an average of about 1,000 weekly active proxies in over 80 countries, however we believe their true bot population is less than advertised to potential users.”
The operation was initially discovered by CERT Orange Polska in 2023 and Lumen spent about a year tracking it. Lumen found that the group is not using zero-day vulnerabilities and typically exploits an array of bugs to take over devices — specifically targeting end-of-life devices with issues dating back years.
The FBI urged people to read through its advisory to see if their brand of router was impacted and replace it with a new model. Users can also reboot the device and disable remote administration.
Compromised routers continue to be a key avenue for Chinese hacking campaigns targeting U.S. critical infrastructure. U.S. officials in recent months have raised alarms about TP-Link routers specifically because they are repeatedly being exploited by Chinese hackers who have used them to breach telecommunications giants.
For years, critical vulnerabilities in routers have been abused by hackers who use them as cover for subsequent attacks or add them to powerful botnets that disrupt websites with bogus traffic.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.