59.4 million compromised payment card records posted for sale on dark web in 2022: report
Nearly 60 million compromised payment card records were posted for sale on dark web platforms in 2022, according to new report.
Researchers with Recorded Future's Insikt Group said the numbers were actually a stark decrease compared to the numbers seen in 2021, which reached almost 100 million compromised payment card records. The Record is an editorially independent unit of Recorded Future.
Hackers physically compromise merchant devices to steal payment card data to facilitate Card-Present (CP) transactions. While cybercriminals typically use digital compromises — often with Magecart e-skimmer infections — to steal card data from online Card-Not-Present (CNP) transactions.
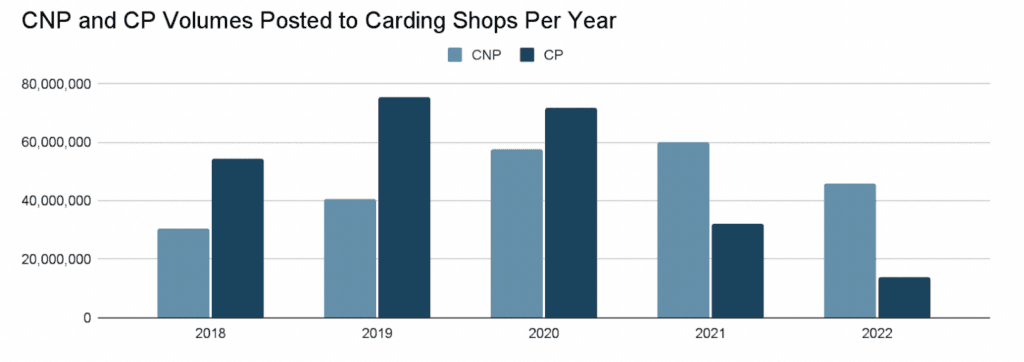
For 2022, Insikt researchers found 45.6 million CNP and 13.8 million CP payment card records posted for sale to carding shops on the dark web. There were 60 million CNP and 36 million CP records in 2021.
“Russia’s cybercrime crackdown — followed promptly by its full-scale invasion of Ukraine — spawned lower carding volumes for the remainder of the year. As war in Ukraine hampered cybercriminals’ ability to engage in card fraud, one top-tier carding shop exploited the lull in supply by flooding the market with recycled payment card records,” the researchers theorized.
“Frustrated by these records’ low quality, resourceful threat actors may nevertheless use them as cheap sources of personally identifiable information (PII) that they can weaponize to carry out targeted account takeover (ATO) attacks against their victims.”
CP breaches in 2022 overwhelmingly affected small restaurants and bars but were down 62% compared to 2021. The researchers said the numbers have steadily declined over the years “due to the rising global adoption of more secure in-person payment methods.”
Contactless payment, EMV chips and the general decrease in in-person transactions have all contributed to the decrease, according to the researchers. The overall decrease in activity was attributed to several raids in January and February 2022 by Russian law enforcement to shut down several top-end carding shops.
“Given that the crackdown occurred during Russia’s troop buildup on the Ukrainian border, the governing theory is that Russia sought to signal its intent to cooperate with the West against cybercrime should the West acquiesce to Russian demands regarding Ukraine,” the researchers theorized.
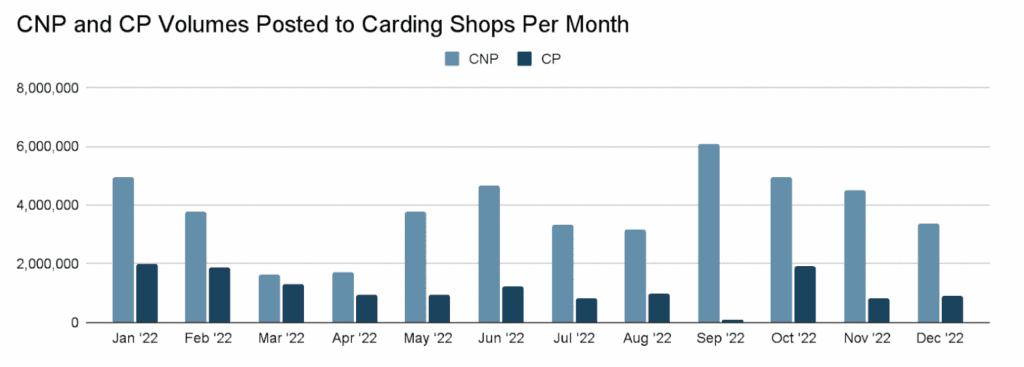
The carding activity rebounded slightly once the invasion began but faced new hurdles – like forums being flooded with “low-quality” cards that had already expired.
There was yet another slump in activity around April, with the war likely inhibiting the ability of actors in Ukraine and Russia to continue normal levels of card fraud activity.
The researchers said Russian-occupied areas of the Donbas region of Ukraine were long suspected to have hosted cybercriminal server infrastructure and the damage done to internet infrastructure – on top of the danger of war and migration – likely contributed to the decrease.
CNP mostly targeted online ordering platforms – Recorded Future’s Magecart Overwatch discovered 1,520 unique malicious domains involved in the infections of 9,290 unique e-commerce domains at any point in 2022. Most involved campaigns that saw groups use fake payment card forms or take over legitimate merchant web infrastructure to install e-skimmers.
In one January 2022 campaign, a gang the researchers call Magecart Group 7 launched a campaign where they infected 1,141 websites.
Nearly 900 e-commerce domains have been infected with two e-skimmer variants exploiting Google Tag Manager (GTM) – a legitimate web service used for internet marketing, website usage metrics, and customer tracking.
The researchers said merchants in all 50 states and the District of Columbia were affected, with the heaviest concentrations in major metropolitan areas.”
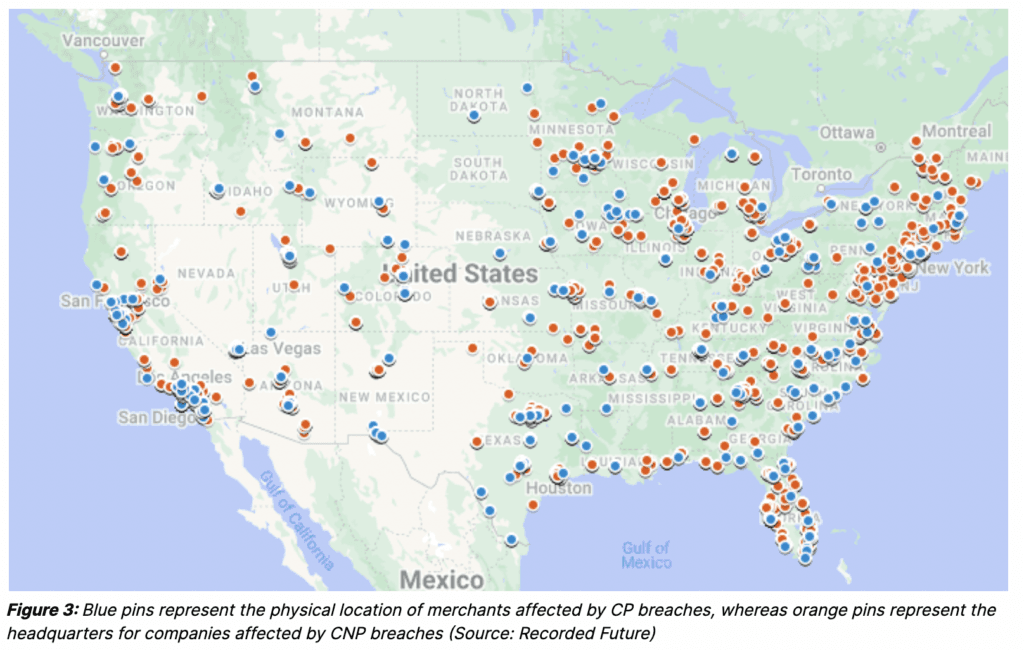
“Through collaboration with partner financial institutions, Recorded Future reported breaches that exposed customer payment card data at over 1,000 unique merchants in 2022. For 77% of the merchants, we have identified compromised payment cards from the breaches on the dark web,” they said.
The biggest hacks involved the compromise of websites used for online ordering solutions for restaurants and ticketing solutions for entertainment and transportation companies – including sites like MenuDrive and Harbortouch.
Just one Magecart campaign in January infected 80 restaurants using MenuDrive and 74 using Harbortouch. InTouchPOS faced its own Magecart campaign that resulted in e-skimmer infections for 157 restaurants using the platform, according to the report.
Payment card data from transactions at 45 amusement parks was exposed when Core Cashless, an online ticketing platform for amusement parks, was breached. The company acknowledged the breach three months after Recorded Future reported it in July 2022.
In total, the researchers found at least 20.5 million records that had full primary account numbers on dark web forums, pastebins, and social media. Once numbers are verified, hackers either conduct fraudulent transactions or get more personal information that would allow them to fully take over a financial account to withdraw funds.
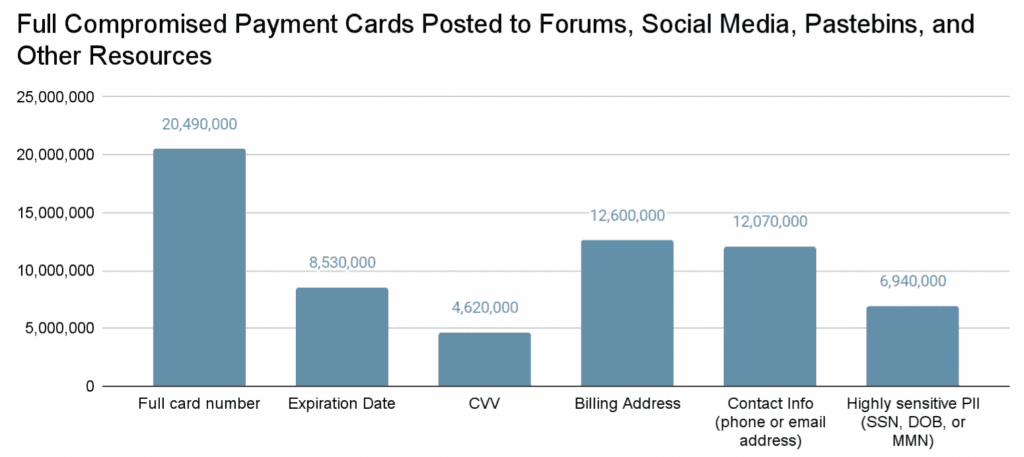
Recorded Future noted that most hackers who get the compromised payment cards are not the same ones who use it for fraud, typically selling it off in ”carding shops.”
“Payment card fraud is an unpredictable, time-consuming process. Fraudsters must operate logistical networks, resell goods and services, devise and execute cash-out schemes, and launder their criminal profits,” the researchers said.
“In 2022, the average infected website saw 5,215 monthly visitors, and according to e-commerce platform BigCommerce, average customer conversion rates range from 2.5 to 3%. If threat actors collect between 130 to 160 cards per month from each of their infected websites, then sell them at an average price of $15 USD per compromised card, they could easily rake in between $1,950 and $2,400 USD per month, per infected website.”
In 2022, 70% of the 59.4 million compromised payment card records were issued by financial institutions in the United States.
Recorded Future predicted that in 2023, the card fraud market will be similarly dependent on world events – arguing that the outcome of the Russia-Ukraine war will likely determine activity.
“Should war continue, threat actors’ ability to engage in card fraud will likely remain degraded,” the researchers said. “Should it end, a renewal or increase in payment card fraud may follow.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



