3 Ways Hacks Exploiting the COVID-19 Crisis Have Evolved
Over the last year, the COVID-19 pandemic has been punctuated by a series of crises and developments: In February, the U.S. declared a public health emergency; In March, the economy contracted and unemployment skyrocketed; Relief packages were both passed and stalled in Congress throughout the year; And by December, vaccines were given emergency approval.
With each of these events, hackers altered their techniques in an effort to capitalize on pandemic fears, according to a report released today by Recorded Future. Cybercriminals made use of phishing lures, ransomware, low-level scams, and business email compromise schemes when it suited their needs and created a money-making opportunity. State-sponsored threat actors were also highly active, targeting vaccine research and spreading misinformation about vaccines developed abroad.
Looking ahead: By tracking how cybercriminals and nation-state hackers exploited different stages of the COVID-19 pandemic, researchers say that organizations and cybersecurity professionals can better prepare for threats going forward. “These developments with COVID-19 have been the biggest disruptor to the global economy and cybersecurity landscape, and threat actors took advantage of it,” said Charity Wright, a cyber threat intelligence analyst who co-authored the report. “By studying it, it helps us understand how these attacks will evolve in the future.”
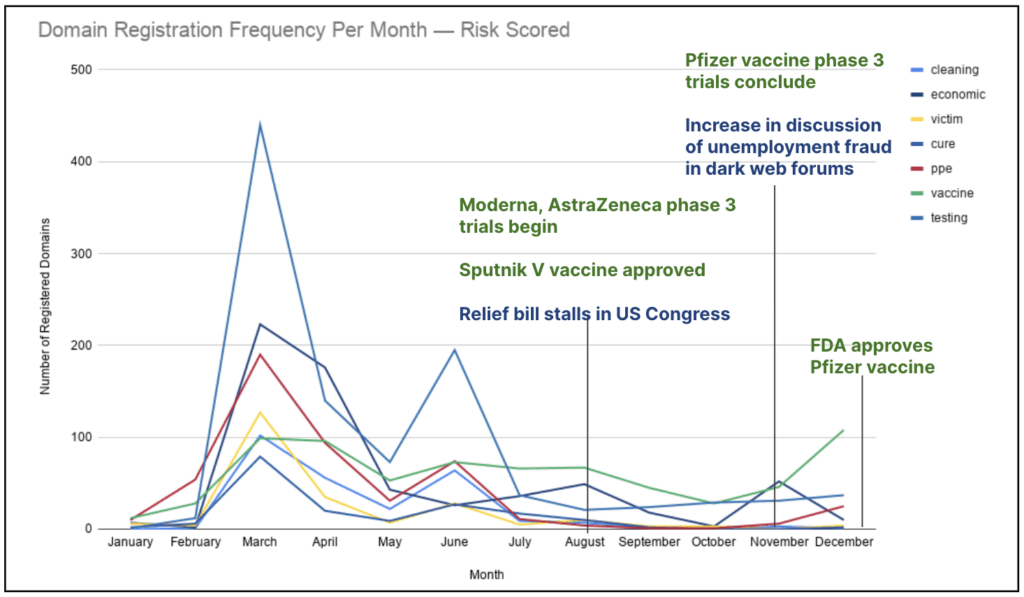
- Cybercriminals register new domains when there are news events that they can capitalize on.
- The majority of domains related to COVID-19 were registered in March, according to Recorded Future data, but there have also been spikes around the times that vaccines start trials and win approvals, as well as when discussions about stimulus bills reach a high point.
- Last month, the U.S. Attorney’s Office for the District of Maryland seized two websites that purported to be related to actual biotechnology companies developing COVID-19 treatments. Instead, the sites were used to collect information from visitors, with the goal of using the data for fraud, phishing attacks, and malware deployment, according to the Department of Justice.
- “At the beginning, the lack of information was the big thing cybercriminals exploited. What is the government doing, where can I get information?” said Lindsay Kaye, director of operational outcomes at Recorded Future and a co-author of the research. “Right now the focus is vaccines, but a couple months from now it will be something different. You need to keep track of what's trendy.”
Hackers have also changed their targets over the last year, especially when they saw new opportunities for scams and fraud.
- Personal protective equipment makers were targeted early on with phishing attacks, scams, and business email compromise schemes.
- Several hospitals in the U.S. and Germany were directly targeted with ransomware. Researchers say that the attackers were going after hospitals because they would be highly incentivized to pay a demand during the pandemic.
- Drug researchers were also a popular target of state-sponsored attackers. Iranian hackers were blamed for attempting to harvest credentials, including passwords, from the maker of Remdesivir in April.
According to the researchers, the vaccine ecosystem is currently the main focus of attackers—state-sponsored hackers, in particular, are trying to steal vaccine information, and some are trying to discredit vaccines developed in other countries.
Threat actors have also transitioned from directly targeting the makers of vaccines to focusing on companies in the wider vaccine supply chain. In some of these cases, cybercriminals are hoping to make money by threatening to delay the vaccine roll-out.
- Cold storage companies, which are essential to keeping vaccine doses at the appropriate temperature, have been targeted by ransomware attacks and phishing campaigns, according to the report.
- Organizations involved in clinical trials have also been targeted. Dr. Reddy’s Laboratories, a pharmaceutical company based in India, was hit by a ransomware attack after receiving approval to conduct clinical trials, for example.
- Vaccine distributors have also faced unique challenges. Scams have gathered victim’s health and financial information by offering early access to the vaccine, and fake vaccines have been advertised for sale on the dark web—Recorded Future said it has no evidence that these vaccines are legitimate or have been diverted from intended recipients.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



