129 Dell models, including Secured-core PCs, vulnerable to new firmware flaws
Around 129 Dell consumer and business laptops, desktops, and tablets, including devices protected by Secure Boot and Dell Secured-core PCs, have been found to be vulnerable to a series of vulnerabilities that can allow threat actors to pass as the official dell.com domain and trigger malicious BIOS/UEFI firmware updates.
As part of a coordinated vulnerability disclosure process, Dell has released security updates today to address the four security flaws, all discovered by Eclypsium, a US-based security vendor specialized in firmware analysis.
More precisely, the four security flaws impact a feature named BIOSConnect that is part of the Dell SupportAssist utility that is usually preinstalled on all Dell devices.
The BIOSConnect feature allows device owners to recover systems where a hard drive failure occurred by connecting to the Dell domain and triggering a network-based SOS boot recovery.
In a report shared with The Record this week, Eclypsium researchers said that if attackers can obtain a Machine-in-the-Middle (MitM) position where they can tamper with the victim's traffic, the four vulnerabilities they discovered can allow the attacker to tamper with the BIOSConnect encrypted HTTPS traffic and then deliver a malicious update to a Dell device.
While the conditions for such an attack scenario are hard to pull off, Eclypsium says they are well worth the effort for a threat actor as BIOSConnect can provide full control over a victim's device by overwriting the BIOS/UEFI firmware.
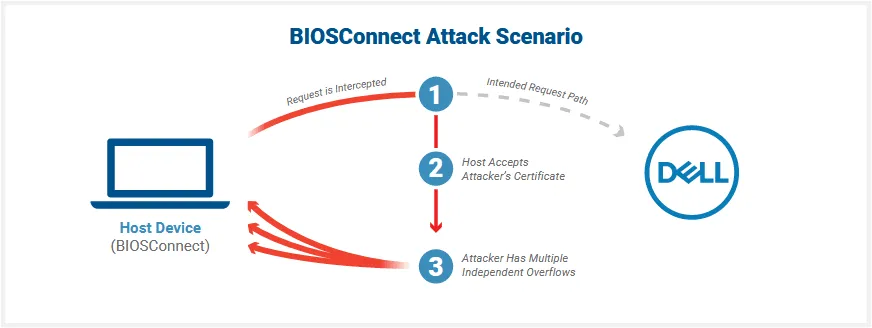
Per the research team, the following vulnerabilities can be abused in these types of attacks:
- Insecure TLS Connection from BIOS to Dell - When attempting to connect to the backend Dell HTTP server, the TLS connection from BIOSConnect will accept any valid wildcard certificate.
- Overflow Vulnerabilities Enabling Arbitrary Code Execution - With the ability to impersonate Dell, the attacker can deliver malicious content back to the victim machine. Three bugs in this update process allow the attacker to execute code in the BIOS. The three bugs are independent of one another and can be exploited with the same results.
"Successfully compromising the BIOS of a device would give an attacker a high degree of control over a device," the Eclypsium team said.
"The attacker could control the process of loading the host operating system and disable protections in order to remain undetected. This would allow an attacker to establish ongoing persistence while controlling the highest privileges on the device."
Please refer to the Dell advisory for the full list of affected models. Rough calculations would indicate that around 30 million Dell devices are impacted by these vulnerabilities.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



