Email security loopholes are latest path for North Korean social engineering attacks
Hackers connected to the government of North Korea are exploiting loopholes in email security systems to send spoofed messages that look legitimate, allowing them to pose as journalists or academics.
Several federal agencies, including the FBI, NSA and State Department, published an advisory this week warning that hackers within the Kimsuky operation are targeting improperly configured DNS Domain-based Message Authentication, Reporting and Conformance (DMARC) record policies.
DMARC, more than a decade old, is a security tool used by email platforms to authenticate messages and make it so popular domains cannot be spoofed. Successful DMARC implementations block malicious emails that attempt to look like they came from verified organizations. Depending on the configuration, an email that fails a legitimacy test can be marked as spam or blocked.
According to the agencies, North Korean hackers are targeting improperly configured DMARC setups to make it look like their emails are coming from a legitimate domain’s email exchange, allowing them to masquerade as experts or academics with credible links to North Korean policy circles. The campaign tracked by the agencies ran from the end of 2023 into early 2024.
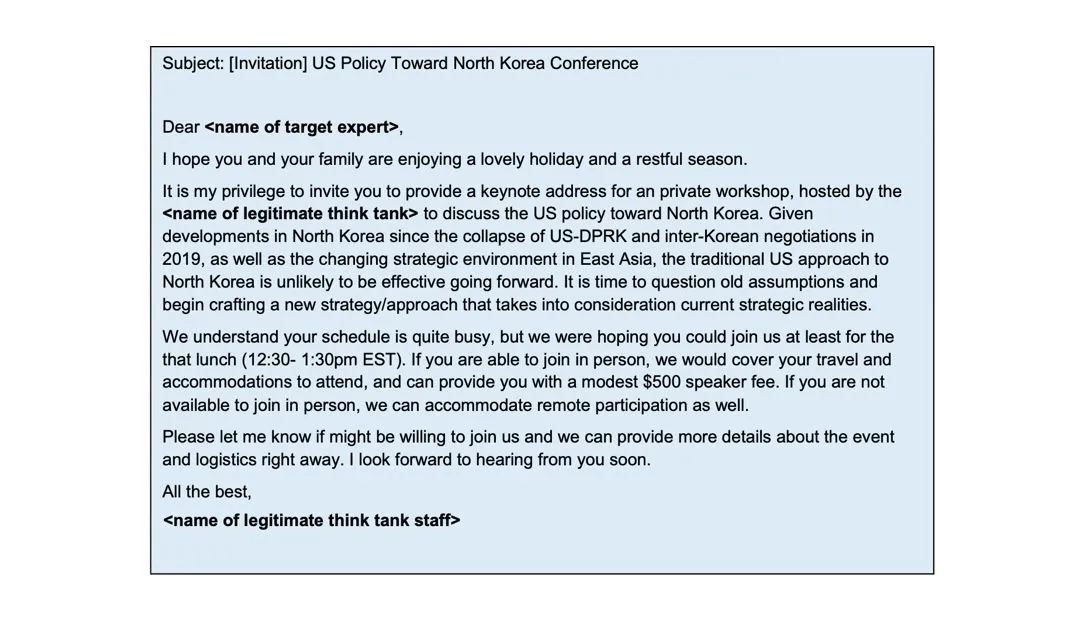
Sample email from Kimsuky campaign. Image: FBI
In one example included in the advisory, a speaker fee is offered to the victim as a way to get them to open the email. Some emails show evidence that North Korean hackers were able to gain access to a university’s legitimate email client to send the email.
But most of the other emails spoofed the name of a legitimate journalist and real email domain yet still were able to get into an inbox due to an organization not having any DMARC policy.
“North Korea leverages these spearphishing campaigns to collect intelligence on geopolitical events, adversary foreign policy strategies, and any information affecting North Korean interests by gaining illicit access to targets’ private documents, research, and communications,” the agencies said.
Kimsuky is a hacking group law enforcement agencies believe is operated out of the 63rd Research Center within North Korea’s Reconnaissance General Bureau (RGB). The group’s goal is to maintain “provide stolen data and valuable geopolitical insight to the North Korean regime by compromising policy analysts and other experts.”
The hackers spend time researching victims and tailoring spearphishing emails to “appear more realistic and appealing to their targets.” They often use content from emails of previously compromised email accounts to enhance the seeming authenticity of their spoofed emails, according to the US agencies.
“In addition to convincing email messages, Kimsuky cyber actors have been observed creating fake usernames and using legitimate domain names to impersonate individuals from trusted organizations, including think tanks and higher education institutions, to gain trust and build rapport with email recipients,” the advisory said.
If someone became suspicious of an email and checked the “reply-to” section, it would still appear to come from a legitimate domain.
Anyone in the US or South Korea working on North Korea, Asia, China, and/or Southeast Asia matters should be on the lookout for the emails — particularly government officials and military members.
The advisory warns people to be wary of emails with innocuous initial communication followed by strange links or attached documents from different email addresses.
North Korean actors have long been accused of impersonating journalists and researchers in an effort to break into the systems of organizations. SentinelLabs published a report in January highlighting a campaign aimed at experts in North Korean affairs from South Korea’s academic sector, as well as a news organization focused on North Korea, SentinelLabs said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

