Two million database servers are currently exposed across cloud providers
It's become somewhat of a tech meme in recent years that cloud service providers have intentionally designed the user interface of their administrative panels in order to confuse customers and bill them for more services than they initially wanted to buy or use.
While never proven to be a formal business strategy, in recent years, the internet has been flooded with news and data breach notifications that have originated after a company misconfigured a cloud-based database, which eventually leaked sensitive data online.
A 2020 study from the Cloud Security Alliance confirmed that companies viewed server misconfigurations as their primary risk in terms of cloud security.
However, just because companies are aware of an issue doesn't mean that they are successful at avoiding exposing their cloud servers online either by accident or lack of awareness of a security control's real function.
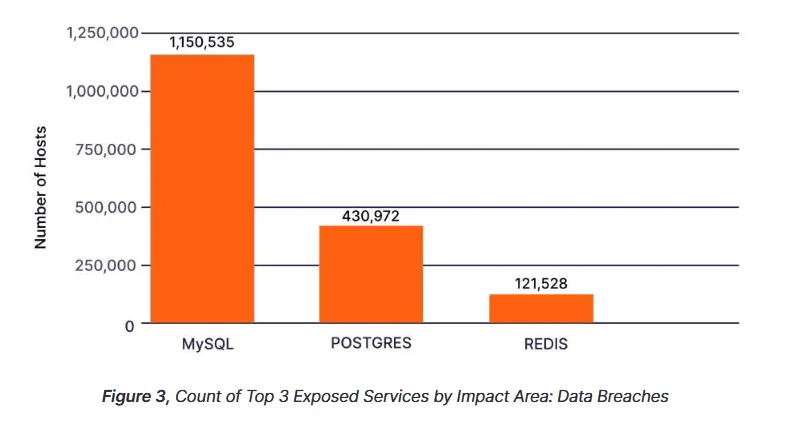
60% of exposed DBs are MySQL servers
Last month, Censys, a security firm specializing in internet-wide census-like scans, took a closer look at the services that were left exposed on the infrastructure of cloud providers, seeking to discover what would be the most possible source of a misconfiguration for companies running cloud-based systems.
In particular, Censys researchers looked at two categories of exposures: databases and remote access software.
According to its report, published this week, Censys said it found more than 1.93 million databases on cloud servers that were exposed online without a firewall or other security protections.
The security firm argues that threat actors could discover these databases and attack them using exploits for older vulnerabilities and gain access to their data.
Furthermore, if the database was exposed by accident, the chances were that it is also using a weak or no password at all, exposing its entire contents to anyone who discovered its IP address.
Censys said it scanned for MySQL, Postgres, Redis, MSSQL, MongoDB, Elasticsearch, Memcached, and Oracle databases and found that almost 60% of all exposed servers were MySQL databases, which accounted for 1.15 million of the total 1.93 million exposed DBs.
1.93 million cloud servers are exposing RDP login pages online
But the security firm also scanned if cloud service providers were exposing ports typically used by remote management software, such as SSH, RDP, VNC, SMB, Telnet, Team Viewer, and PC Anywhere.
While the innate feature of these apps is to provide a way to log into systems remotely, Censys argued that access to these remote management ports should not be easily discoverable but instead protected by access control lists, VPN tunnels, or other traffic filtering solutions.
Such protections are usually available in the dashboards of many cloud service providers, but it appears that not many customers knew how to enable such protections, as Censys found millions of exposed remote management ports.
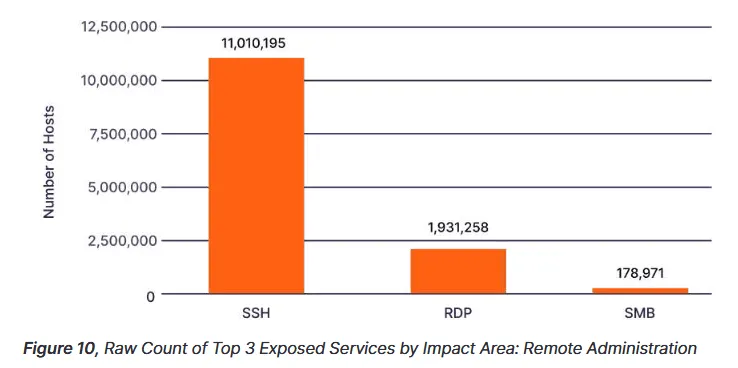
The most notable discovery was that more than 1.93 million servers were exposing RDP login screens online.
This was a significant discovery as Microsoft, and multiple security firms, have been screaming at the top of their lungs for the past five years, asking companies to secure RDP endpoints behind firewalls.
Microsoft and others have often pointed out that many security breaches have often originated with attackers gaining access to a company via compromised RDP credentials. This included attacks from a wide array of threat actors, from DDoS botnets to crypto-mining operations and from ransomware gangs to state-sponsored actors.
Some of the reasons behind these misconfigurations
Censys believes that companies and their IT staff should have been more than aware of these risks by this point in time due to previous public breaches, but other factors intervened.
One of these reasons is that most companies don't run internal networks using the infrastructure of just one cloud service provider but usually tend to use multiple solutions, many of which don't have the same controls or default configurations, allowing a few systems to become exposed even when IT staff never intended.
Second, while some cloud providers have taken steps to simplify their dashboards and explain how some controls work, there is still a significant difference between the vocabulary of each cloud provider, which tends to still confuse some system administrators.
As the cloud market usually sees companies rise and fall, Censys said it expects the issue of misconfigured services to remain a big problem for companies going forward.
The issues discovered and discussed in the Censys report are also not new. A similar study from mobile security firm Zimperium, published last month, found that 14% of all mobile apps used a cloud storage solution that was misconfigured and exposed the app's users data.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

