State-of-the-art EDRs are not perfect, fail to detect common attacks
A team of Greek academics has tested endpoint detection & response (EDR) software from 18 of today's top cybersecurity firms and found that many fail to detect some of the most common attack techniques used by advanced persistent threat actors, such as state-sponsored espionage groups and ransomware gangs.
"Our results indicate that there is still a lot of room for improvement as state-of-the-art EDRs fail to prevent and log the bulk of the attacks that are reported in this work," said George Karantzas and Constantinos Patsakis, two academics from the University of Piraeus, in Athens, Greece.
Typical attack scenario
The research, detailed in a paper published last year and titled "An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors"[PDF], looked at EDR software, which is an evolution of the classic antivirus program that operates using both static and dynamic analysis methods to detect malware, but also monitors, collects, and aggregates data from endpoints in an attempt to detect malicious behavior that relies on more stealthy techniques, such as abusing legitimate apps to carry out attacks.
Today, EDRs combine everything from static file signature rules to advanced machine learning modules and are considered the top of the food chain in regards to security software. However, they are not perfect.
Karantzas and Patsakis' research set out to find out how the EDRs from some of today's largest companies fair in the face of various simple attacks that simulate common APT kill chains.
Their work included buying a mature expired domain to host malware payloads, securing the domain with a Let's Encrypt SSL certificate, and hosting four types of files commonly used in attacks, such as:
- A Windows Control panel shortcut file (.cpl);
- A legitimate Microsoft Teams installer (that will load a malicious DLL);
- An unsigned portable executable (EXE) file;
- An HTML application (HTA) file.
Once executed, these four files would all abuse legitimate functions to load and run a Cobalt Strike Beacon backdoor.
The idea behind this attack chain is that these four files and the Beacon backdoor are regular payloads typically sent to victims part of spear-phishing email campaigns—and something that all EDRs are expected to either detect, block, or at least alert security teams when deployed inside corporate networks.
Tested EDRs and results
The research team tested these attacks against EDR software from Bitdefender, Carbon Black, Check Point, Cisco, Comodo, CrowdStrike, Elastic, ESET, F-Secure, Fortinet, Kaspersky, McAfee, Microsoft, Panda Security, Sentinel One, Sophos, Symantec, and Trend Micro. The results are in the table below:
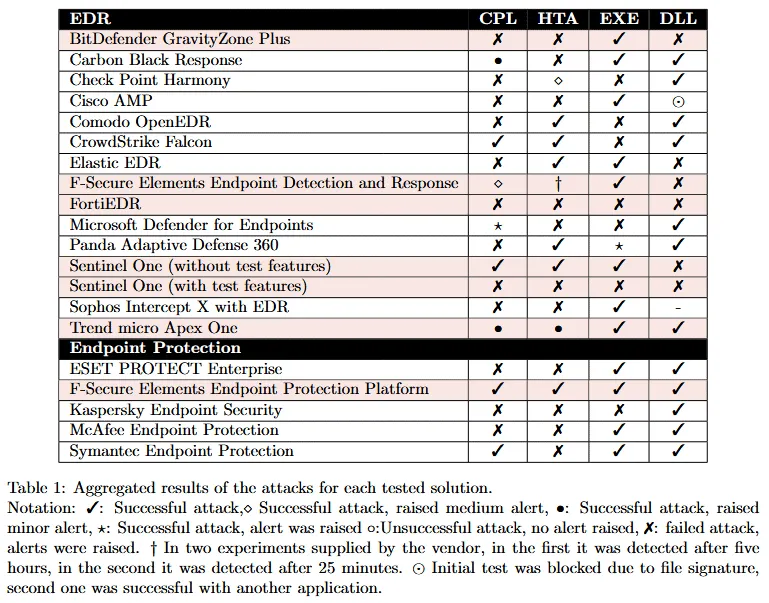
The results show that only two of the tested EDRs had full coverage for all attack vectors, allowing threat actors a way to slip through a company's defenses.
The research team argued that this opens the EDRs to situations where attackers could turn them off or at least disable their telemetry functions, effectively blinding defenders to what may be happening on an infected system and allowing threat actors to prepare further attacks on the local network.
But not all EDRs were tested part of this experiment.
Appearing last year in a vlog on the YouTube channel of John Hammond, a senior security at Huntress Labs, the researchers said that not all EDR vendors agreed to open their products for testing, and even some of the 18 products they tested was done with the help of intermediaries such as SOC and CERT teams.
However, Karantzas and Patsakis said that once their research went live, some vendors reached out and inquired about it and the ways they could improve their products.
Article updated shortly after publication to include the results of an expanded versions of the research, which analyzed an additional seven EDRs, on top of the original 11.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

