REvil gang shuts down for the second time after its Tor servers were hacked
The REvil ransomware group has shut down its operation for the second time this year, claiming in a message posted on an underground hacking forum that they lost control over their Tor-based domains.
The group, considered one of the most successful ransomware operations to date, had been active since April 2019.
They shut down for the first time on July 13 this year, after one of their attacks against Kaseya servers during the July 4th US holiday hit thousands of businesses—in an incident that drew veiled threats and the attention of White House officials.
The decision to shut down operations was taken by the group's leader and public figure, an individual named UNKN, who took down servers and disappeared with the group's money, which left them unable to pay many of their affiliates—other groups who were helping REvil execute attacks and were splitting the profits.
The group, minus UNKN, made a formal return in early September using the same REvil name. To prove they were the same group as before, this new REvil incarnation restored all of their former Tor-hosted portals, such as their victim payment/extortion portal and data leak site.
As soon as they returned, the group's members began launching new attacks.
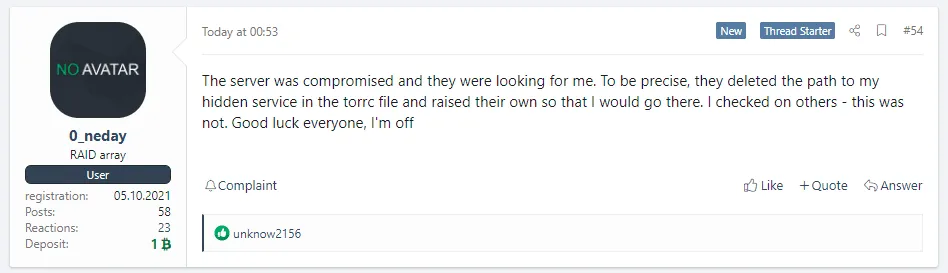
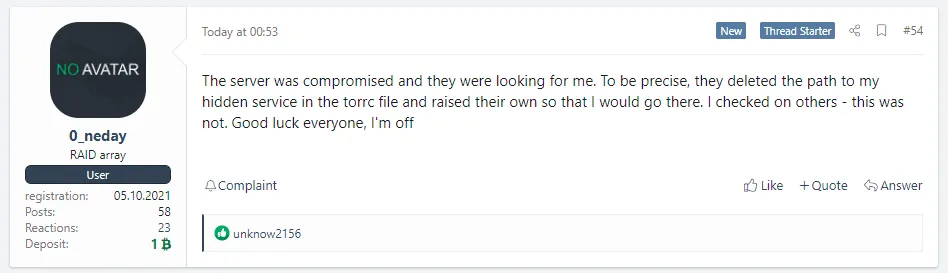
But this Sunday, in a series of messages spotted by Recorded Future analyst Dmitry Smilyanets, the group's new administrator, an individual named 0_neday, said that a third party compromised their Tor-based portal.
"The server was compromised and they were looking for me," 0_neday said in a message, also translated and screenshoted below.
"To be precise, they deleted the path to my hidden service in the torrc file and raised their own so that I would go there," 0_neday added, suggesting someone had created a clone of the legitimate REvil Tor backend panel.
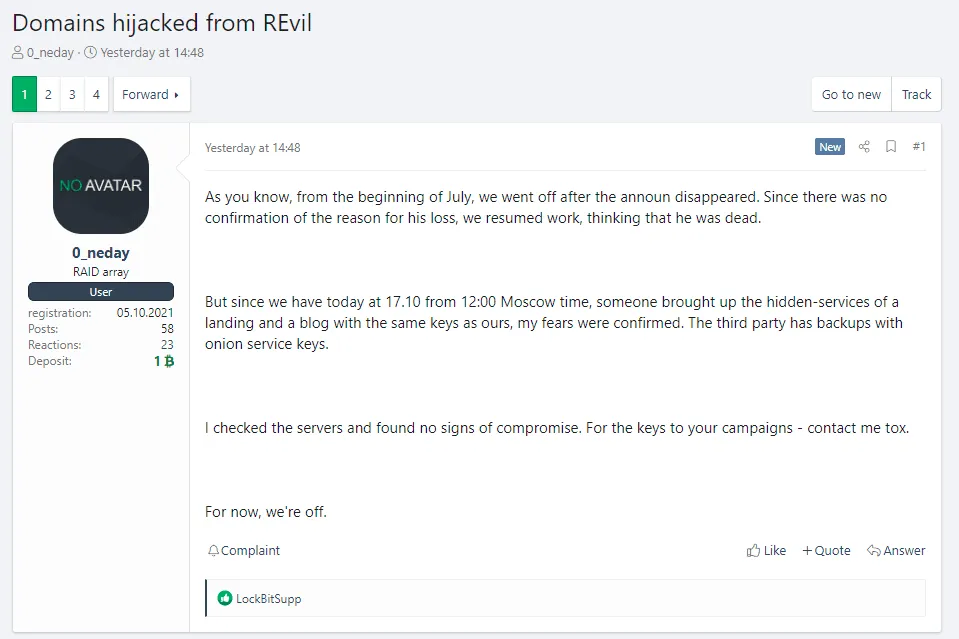
The REvil server compromise came at a terrible time for this new incarnation of the REvil group, which was still dealing with the aftermath of their July shutdown.
Several affiliates were still trying to recover funds stolen by UNKN, the gang's first admin, and the group's developers were also accused of hiding a backdoor inside their code. The backdoor allegedly allowed the REvil admins to provide decryption keys to victims directly and force affiliates out of ransom negotiations and their ransom payment cut.
Since the cybercriminal underworld is mainly driven by reputation and trust, the writing was on the wall for 0_neday, who at this point chose to shut down the REvil operation for good, rather than deal with the gang's ever-increasing bad reputation, most likely entirely gone after having its servers compromised over the weekend.
“I really hope we just witnessed an offensive operation by the US government," Smilyanets told The Record. "That is how you deal with cybercriminals - using their own methods against them. Release the Hounds!”
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.