New HolesWarm botnet targets Windows and Linux servers
A new botnet named HolesWarm has been slowly growing in the shadows since June this year, exploiting more than 20 known vulnerabilities to break into Windows and Linux servers and then deploy cryptocurrency-mining malware.
While attacks have primarily been spotted across China, with reports from security firm Tencent and various IT bloggers, the botnet is expected to expand its reach, and target systems across the globe as its infrastructure and attack capabilities expand in the coming months.
Primarily operated from a command and control server located at m[.]windowsupdatesupport[.]org, the botnet has been seen exploiting vulnerabilities in software such as:
- Docker
- Jenkins
- Apache Tomcat
- Apache Struts (multiple bugs)
- Apache Shiro
- Apache Hadoop Yarn
- Oracle WebLogic (CVE-2020-14882)
- Spring Boot
- Zhiyuan OA (multiple bugs)
- UFIDA
- Panwei OA
- Yonyou GRP-U8
While the entry vectors may vary per victim, Tencent Security says that once the malware gets a foothold on an infected system, HolesWarm dumps local passwords, expands to the local network, and then deploys an XMRig-based cryptocurrency mining tool.
While other botnet operators try to hide their presence on infected systems by tethering the crypto-mining process, HolesWarm doesn't appear to employ this safety mechanism, and per several reports, the botnet often maxs out server CPUs, leading to its discovery.
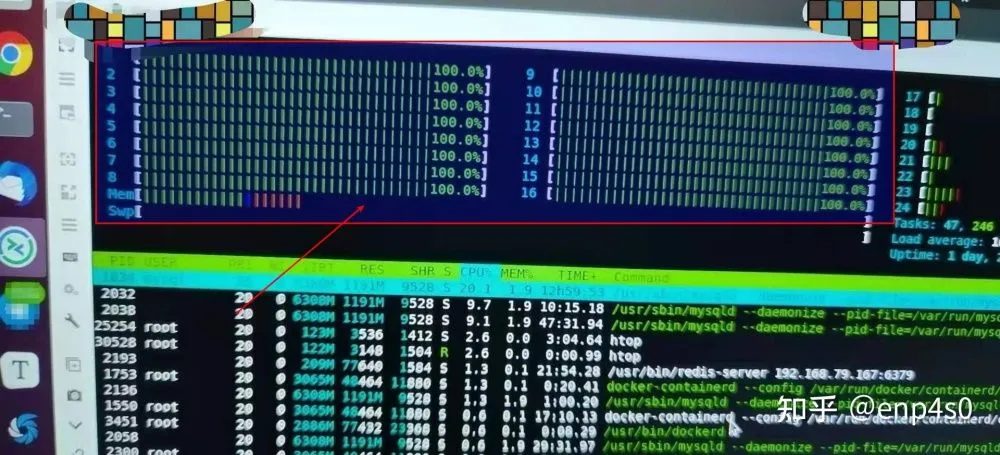
Right now, the botnet is just the latest in a long line of crypto-mining botnets that are popping up online on a regular basis. Nothing in its make-up screams technical sophistication, and the HolesWarm operators are just the latest malware coders taking advantage of the large number of servers running out-of-date software.
IOCs are available in the reports linked above, and in the Twitter thread below, from security firm Intezer Labs, which also saw some of the botnet's earlier attacks.
[1/5] XMRig miner dropper, written in Golang, targets both Windows and Linux. The Linux dropper has no detections in VirusTotalhttps://t.co/CiZEG2vUXk
— Intezer (@IntezerLabs) June 8, 2021
Upon execution, the dropper creates persistence and queries the C&C for extra payload over windowsupdatev1.json
->> pic.twitter.com/wV0BhJA5tw
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.