New 5G protocol vulnerabilities allow location tracking
Security researchers have identified new vulnerabilities in the 5G protocol that could be abused to crash network segments and extract user data, such as location information.
The new vulnerabilities have been discovered at the end of last year by AdaptiveMobile, a cybersecurity firm specializing in mobile network security.
Detailed in a 36-page report published this week, the vulnerabilities impact 5G's network slicing mechanism, a feature that allows network operators to split their 5G infrastructure into smaller portions dedicated for particular use cases, such as automotive, healthcare, critical infrastructure, and entertainment services.
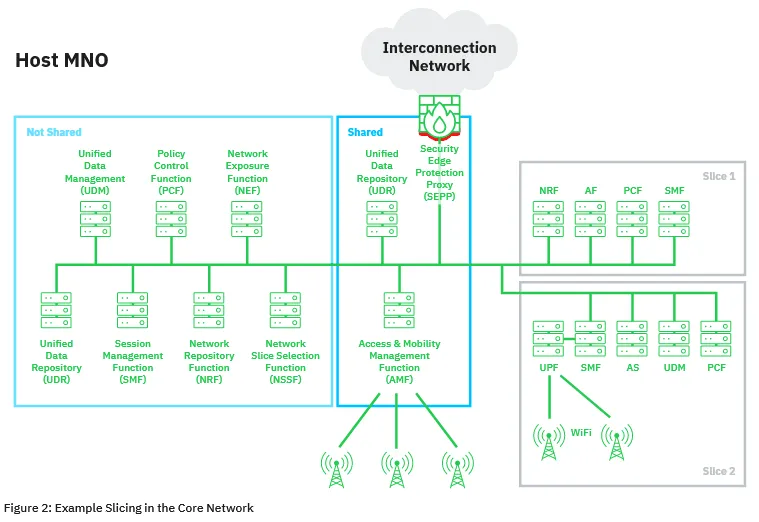
AdaptiveMobile says the vulnerabilities it found can be exploited in hybrid mobile network setups where 5G is mixed with older technologies — network setups that are to be expected in the real world in the coming years as 5G technology rolls out and slowly replaces previous tech.
According to AdaptiveMobile, the attacks are possible because of "a lack of mapping between the application and transport layers identities," which allows attackers to impersonate legitimate network functions in hybrid 5G networks.
This opens the door to situations where if an attacker manages to compromise an operator's edge network equipment, they could abuse 5G protocol functions to launch denial of service attacks against other network slices or extract information from adjacent 5G network slices, including customer data such as location tracking information.
Furthermore, there could also be scenarios where partners who were granted access to network slices could abuse this privilege to attack other sections.
Improvements coming to future 5G standard
The security firm said it notified both the GSM Association (GSMA), an industry group for mobile operators, and the 3rd Generation Partnership Project (3GPP), the organization in charge of developing the 5G standard, of the vulnerabilities it found.
"The full mitigation of the described attacks may require some larger feature development in 3GPP specifications and could potentially be part of Release 17," AdaptiveMobile said.
Release 17, or Rel-17, is the version of the 5G standard that is currently in development and is expected to be released in mid-2022.
What I've been up to lately. Having a very close look at the specifications on how network slicing deep down works in a scenario where part of the infra is shared. Using IT for telco is a steep learning curve for all. #5G https://t.co/PkkLFI9tS8
— Silke Holtmanns (@SHoltmanns) March 24, 2021
AdaptiveMobile's research adds to previous work done on the security of the new 5G protocol. Despite being a newer and more modern telecommunications protocol, 5G is often exposed to attacks due to the need to support legacy features so 5G customers could interact with older-gen standards.
One such example is the GPRS Tunnelling Protocol (GTP). In June 2020, security researchers disclosed several GTP vulnerabilities that could be used to attack both 4G and 5G users.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

