Nearly 700 ransomware incidents traced back to wholesale access markets: report
Researchers have traced almost 700 ransomware incidents back to wholesale access markets (WAM) — platforms where people sell access to compromised endpoints, access over various remote protocols such as RDP, and more.
Of the 3,612 attacks in 2021 investigated by analysts from security firm CyberSixgill, 686 involved access to a system logged in to the organization’s domain that had been offered for sale on a WAM within 180 days before the attack.
Eighty-five of those cases involved access to an internal machine that had been compromised within 30 days of the attack.
CyberSixgill was quick to warn that their data was messy and it is difficult to prove causation, but their preliminary findings indicate that wholesale access markets are one of several avenues ransomware attackers use to gain access to a victim's network.
The access available also informs how ransomware actors approach an attack in terms of data exfiltration, social engineering and more, CyberSixgill noted.
“As long as buyers of access generate massive profits with impunity, we can expect these markets to continue their essential contribution to the cybercrime economy,” the researchers said.
CyberSixgill compared WAMs to initial access brokers (IABs) — another major repository for victim access. IABs auction access to companies for hundreds of thousands of dollars while WAMs offer more low-end access to specific compromised endpoints for fees as low as $10.
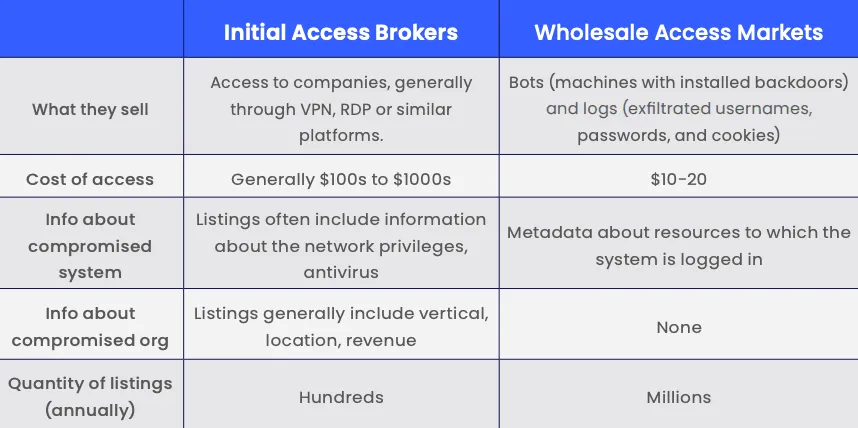
IAB posts on underground forums are typically more detailed than WAMs, providing buyers with information on the victim, how access has been gained, what the access offers a cybercriminal and more.
The IAB sellers are more trusted and typically have reputations they are trying to uphold, while WAMs are effectively flea markets. In 2021, cybercriminals sold more than 4 million compromised endpoints on underground markets, 457% higher than 2020 sales according to CyberSixgill data.
“The prices are low, the inventory is enormous, and the quality is not guaranteed,” the researchers said of WAMs.
“However, just like flea markets, it is possible to find a diamond-in-the-rough. If an actor can buy listings in bulk and just one of them belongs to an enterprise machine, $10 is a minuscule initial investment for an attack that can yield millions.”
In at least 312 cases, an organization was mentioned on multiple markets within 180 days of being breached, meaning the same hackers sold access to victims on several different markets or multiple attackers gained access to the same target.
An example cited in the report is the 2021 ransomware attack on gaming giant EA. In June 2021, the hackers behind the attack purchased access to an endpoint that provided a route to the company’s Slack channel.
Once inside EA’s Slack, they asked the IT department to reset the account's passwords, lying that they lost their phone at a party. They stole 780 GB of data from EA, including the source code for multibillion-dollar gaming franchises like FIFA, Madden, and Battlefield.
Another incident involved a ransomware attack on Bangkok Airways — where access was traced back to someone selling access to an endpoint at the company on August 6, 2021.
By August 28, the airline was attacked by the infamous LockBit ransomware group and more than 200 GB of data was stolen.
Researchers from CyberSixgill warned that even though WAMs are a major tool used by ransomware groups, the majority of cybercriminals taking advantage of the markets are less sophisticated actors.
“We must presume that fewer-step and lesser-sophisticated attacks account for the overwhelming number of attacks that began in wholesale access markets,” they said.
“It takes enormous effort to infect and supply access to 4.3 million endpoints in a year. Therefore, there must be matching demand.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

