Hackers seek to help — and profit from — Iran protests
As protests erupted in Iran over the death in custody of a woman arrested for violating gender-based morality laws, hacker groups started offering help — and sometimes hoped to profit. But researchers warn that the offers may not be as benevolent as they appear.
The cybersecurity firm Check Point said it began observing chatter about the Iranian protests among the groups soon after the death of Mahsa Amini on September 16, when demonstrations broke out.
For the last week, the Iranian government has been limiting mobile internet access from the late afternoon, around 4 pm, to midnight local time, according to Doug Madory, the director of Internet Analysis at Kentik. Although fixed-line internet services remain online, popular services including Instagram and WhatsApp are blocked, he said.
“What we see are groups from the Telegram, dark and also ‘regular’ web helping the protestors to bypass the restrictions and censorship that are currently in place by the Iranian Regime, as a way to deal with the protests,” said Check Point security researcher Liad Mizrachi over email.
The hacker groups congregate in chatrooms with thousands of members, and lately some have been sharing information about Virtual Private Networks (VPNs) or proxy services for use by those in Iran.
Others in the groups appear to be seeking to leak or sell data they claim is connected to the Iranian regime — including alleged information about government officials and maps of sensitive areas, according to Check Point.
Among the groups are cybercriminal operations, including Arvin Club and Atlas Intelligence Group, the company said. Arvin Club is a ransomware outfit with a popular Telegram channel that often shares information related to data leaks. Users frequently post in Persian and the group has previously denied rumors it was cooperating with the Iranian regime, per darknet monitoring service DarkOwl.
Members of the Arvin Club channel shared information about alleged leaks of data about Iran, as well as VPN links and information about censorship evasion via the private browsing tool Tor, according to screenshots shared by Check Point and The Record’s review of the chat.
The channel also changed its image to a black silhouette of Iran with the words “sensitive content” and an eye icon with a line through it.
The cyber mercenary operation Atlas Intelligence Group (A.I.G.), shared information about proxies and a note encouraging protesters to evade censorship, according to Check Point’s research. It also advertised alleged Iranian data for sale. A.I.G. uses an outsourcing approach to its hacking efforts, serving as almost a fixer service between customers and hackers.
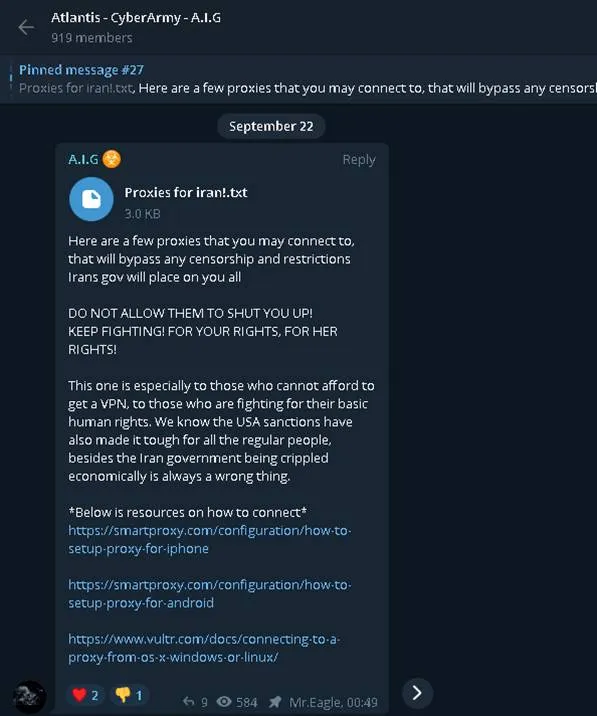
The veracity of documents being leaked or sold by such groups is unclear. As is, ultimately, the safety of some of the help they claim to offer.
In theory, VPNs and proxy services are a way to evade censorship on Iran’s still operational fixed line internet network, according to Madory.
But trusting links to those services offered by cybercriminal organizations may not be the best way to access them.
“The VPN might not be safe, but taking into consideration that it might work to bypass censorship restrictions; many still think it is worth trying,” Mizrachi said. “The risk is that the service will sniff (essentially create a copy of) the traffic and disclose sensitive information. There is also the slim chance that the [Islamic Revolutionary Guard Corps] themselves might try to offer a ‘free VPN’ to entice people to use it so that they can then identify them,” he added.
Andrea Peterson
(they/them) is a longtime cybersecurity journalist who cut their teeth covering technology policy at ThinkProgress (RIP) and The Washington Post before doing deep-dive public records investigations at the Project on Government Oversight and American Oversight.

