Darkside operator involved in supply chain attack via CCTV vendor's website
A cybercrime group that used to cooperate with the Darkside ransomware gang has breached the website of a CCTV camera vendor and inserted malware in a Windows application the company's customers were using to configure and control their security feeds.
The intrusion into the CCTV camera vendor's website took place on May 18 and lasted until early June when security firm Mandiant discovered the malware and notified the affected company.
According to an incident response report published today, Mandiant said the malware was hidden inside a customized version of the Dahua SmartPSS Windows app that the unnamed CCTV vendor was providing to its customers.
If customers downloaded and installed the trojanized application, it would infect a company's systems with a version of the SMOKEDHAM backdoor.
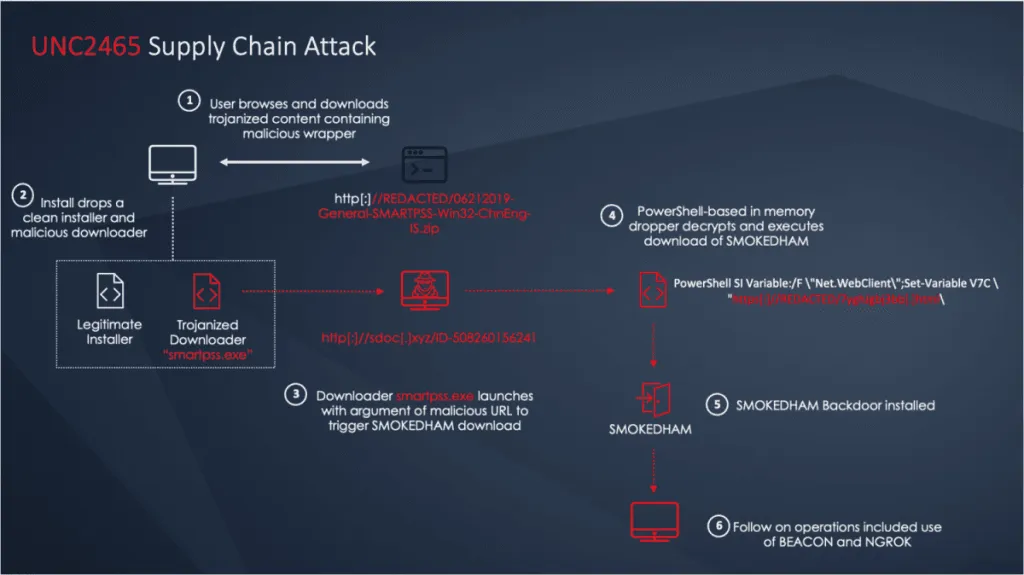
While the Darkside ransomware operation shut down in mid-May in the fallout following the attack on Colonial Pipeline, Mandiant said it was able to link this attack to one of Darkside's three major sub-groups, which the company tracks as UNC2465.
Know as "affiliates," together with UNC2628 and UNC2659, UNC2465 orchestrated intrusions into corporate networks and then deployed the Darkside ransomware, which they rented from the Darkside operators. Once victims paid, UNC2465 would get an 85% cut of the payment and move on to newer targets.
Mandiant said it was able to connect the intrusion into the CCTV vendor's official website to UNC2465 because the infection chain deployed SMOKEDHAM, a backdoor trojan that until now has been exclusively deployed in UNC2465 intrusions.
While UNC2465 did not end up deploying the Darkside ransomware on the internal networks of victims it made in this recent campaign, Mandiant researchers warn that the threat actor may soon pivot to a new RaaS (Ransomware-as-a-Service) and deploy a different ransomware instead.
The company is now urging companies to scan internal networks for the SmartPSS app and search for signs of compromise with the SMOKEDHAM backdoor.
Indicators of compromise and additional details about the infection chain are available in Mandiant's report.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

